之前的文章<<OpenStack私有网络安全防护>>介绍了在私有网络中将虚拟防火墙(以下称为VFW)串联接入的方法。本文来介绍旁路部署VFW, 通过策略路由实现防火墙接入的方法。
逻辑网络拓扑如下:
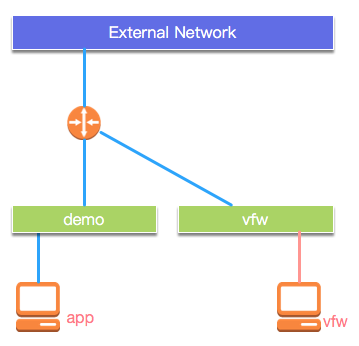
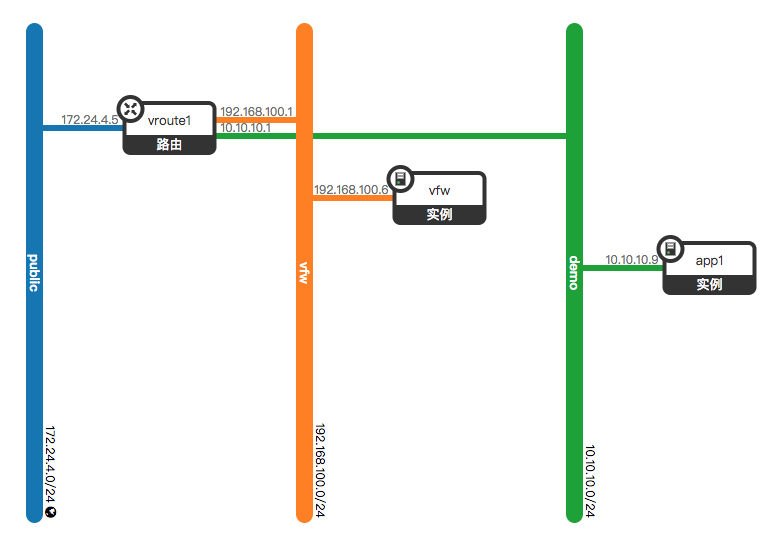
我们在OpenStack环境中创建一个CentOS7的实例来模拟VFW, 部署完网络拓扑如下:
我们需要将CentOS7的路由转发功能开启:
1 | sysctl -w net.ipv4.ip_forward=1 |
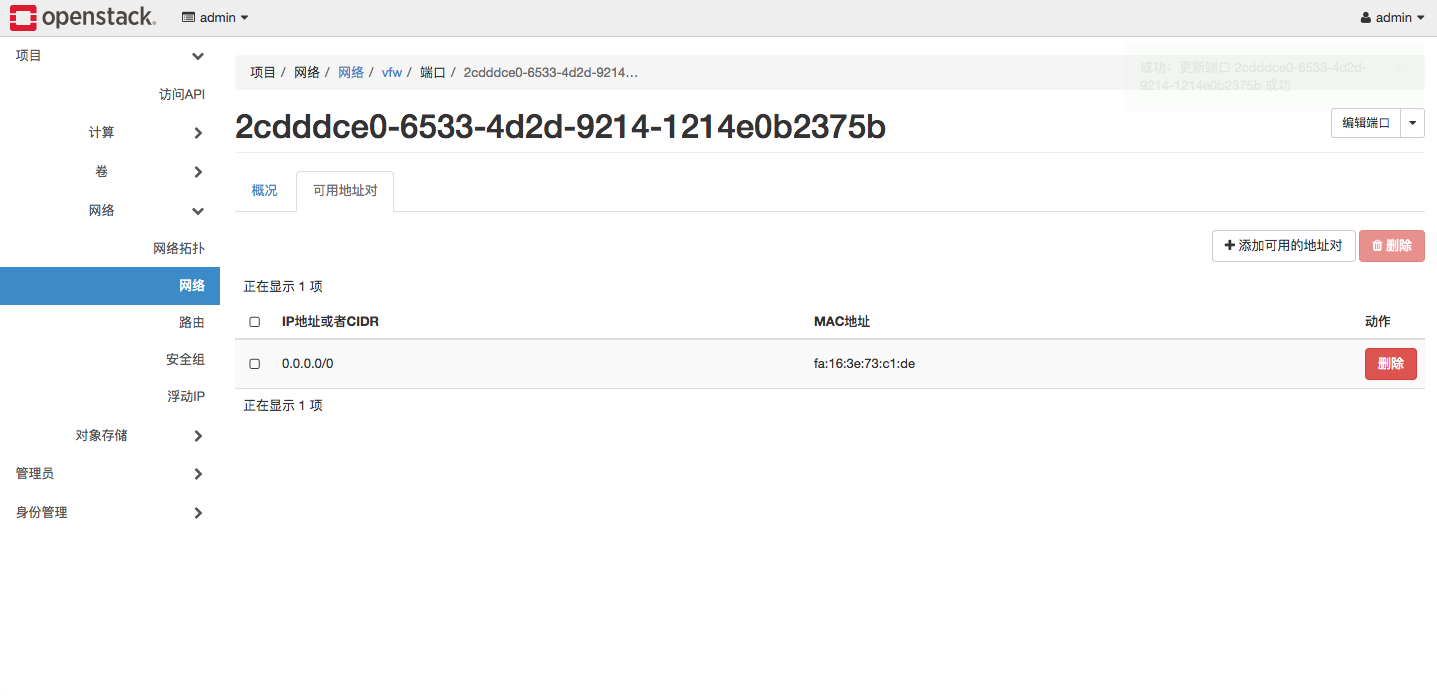
此外,OpenStack网络上有Anti Mac-Spoofing的机制,默认情况下,只有数据包的MAC、IP与虚拟机网络接口的MAC、IP相匹配时才允许通过。因而我们需要配置VFW网络接口的可用地址对。将其IP设置为0.0.0.0/0, MAC为接口本身MAC,这样将允许所有数据包通过,如下图所示:
为了将VFW串入网络路径中,我们需要在拓扑图中私有网络demo的vRouter上配置策略路由。OpenStack不支持配置策略路由, 我们只能手动在vRouter的net namespace中配置。
我们登录进vRouter的namespace:
1 | ip netns exec qrouter-b2f289b6-5e7b-4f56-bf5d-ac01629eb333 bash |
查看网络接口:
1 | [root@aio ~]# ip a |
添加一个专用路由表,将默认路由指向VFW所连接的vRouter接口:
1 | [root@aio ~]# ip route add default via 192.168.100.6 dev qr-16448d15-00 table 100 |
添加入方向策略路由:
1 | ip rule add iif qg-c0eea9fd-62 to 10.10.10.0/24 lookup 100 |
添加出方向策略路由:
1 | ip rule add iif qr-a74cdf71-65 lookup 100 |
此时路由规则如下:
1 | [root@aio ~]# ip rule |
我们给虚拟机实例绑定一个浮动IP:172.24.4.4, 然后从外部访问浮动IP,访问成功:
1 | [root@aio ~]# ping 172.24.4.4 -c 2 |
在VFW上的抓包结果也符合预期:
1 | [root@vfw ~]# tcpdump -ieth0 -nn icmp -e |
我们再从业务虚拟机向外访问, 访问却是失败的:
1 | $ ping -c 2 114.114.114.114 |
我的实验环境为All in One环境,在br-ex上抓包发现, 数据包的源IP没有被SNAT策略替换为正确的IP:
1 | [root@aio ~]# tcpdump -i br-ex -nn -e icmp |
这是由于OpenStack的虚拟网络实现上使用IPTABLES规则并依赖CONNTRACK机制实现NAT。SNAT实现上只在CONNTRACK状态为NEW时才会生成NAT所需的状态信息,后续被跳踪的该连接的数据包直接使用生成的NAT状态信息。我们从业务虚拟机向外访问,数据包到达vRouter上的接口时,CONNTRACK模块生成CONNTRACK表项,而此时出口接口为VFW路由接口,并不需要做SNAT,因而不会生成NAT状态信息。而从VFW路由接口再次到达vrouter时,CONNTRACK表项已经生成,不再处理NAT信息,而是直接将数据包发送出去。出入路由外网接口的数据包依赖CONNTRACK机制完成NAT,因而我们不能完全禁用CONNTRACK, 我们只能在业务子网接口和VFW子网接口之间的数据包取消CONNTRACK。
在vRouter中添加如下两条iptables规则来禁用conntrack:
1 | iptables -t raw -A PREROUTING -i qr-a74cdf71-65 -j NOTRACK |
此时,我们再来测试, 访问成功:
1 | $ ping -c 2 114.114.114.114 |
从VFW上的抓包结果可以看出符合预期:
1 | [root@vfw ~]# tcpdump -ieth0 -nn icmp -e |
本文中的VFW接入方式为3层转发模式,而有些厂商的VFW只支持二层透明接入,这种情况下如何在OpenStack环境中应用呢?我后续再来写文章来说明。